Beautiful Work Tips About How To Prevent Conficker
By erik larkin, pcworld apr 6, 2009 12:48 pm pdt.
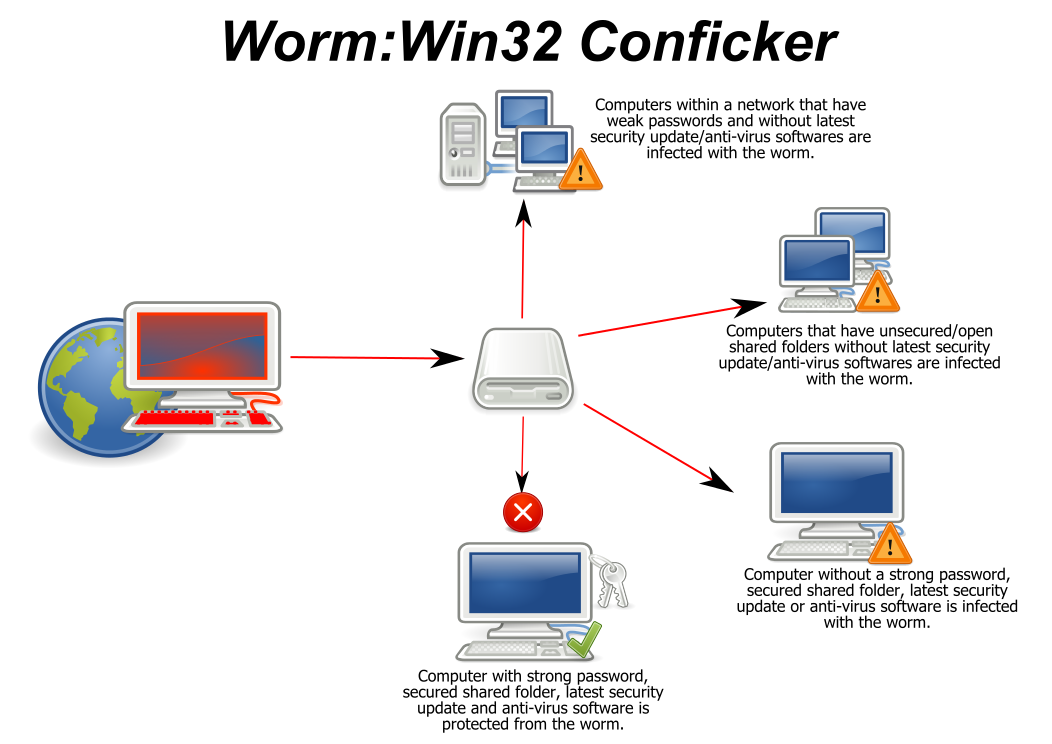
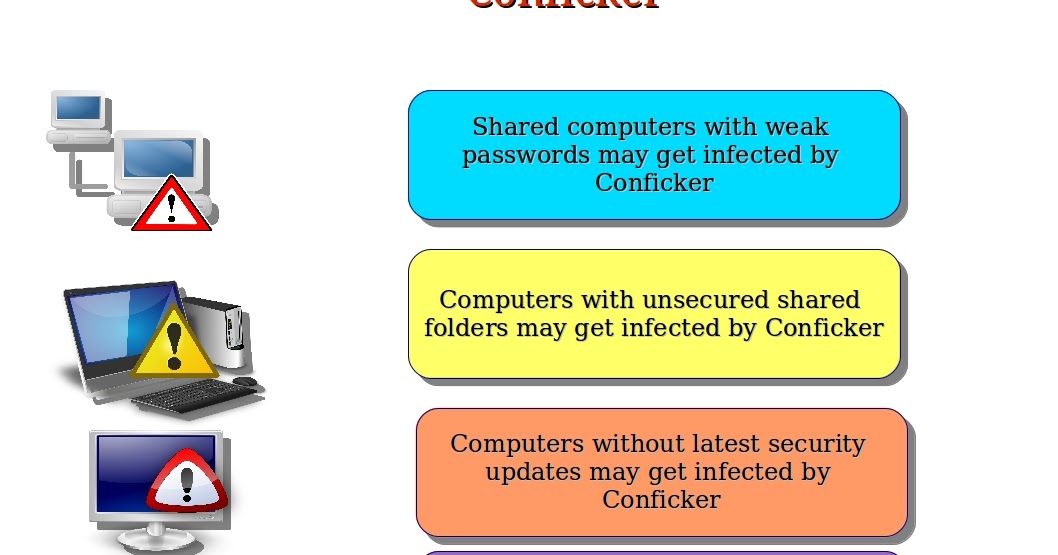
How to prevent conficker. Do not log on to computers by using domain admin credentials or credentials that have access. The last way is to prevent the ability to activate conficker (downadup) by locking the autorun function so that the computer is not infected when connecting to a usb storage. Conficker malware writers made use of domain names rather than ip addresses to make their attack networks resilient against detection and takedown.
How does the conficker virus work? Protecting against this virus can be done by blocking affected ports. A common tactic used by malware is to block the infected computer from connecting to the.
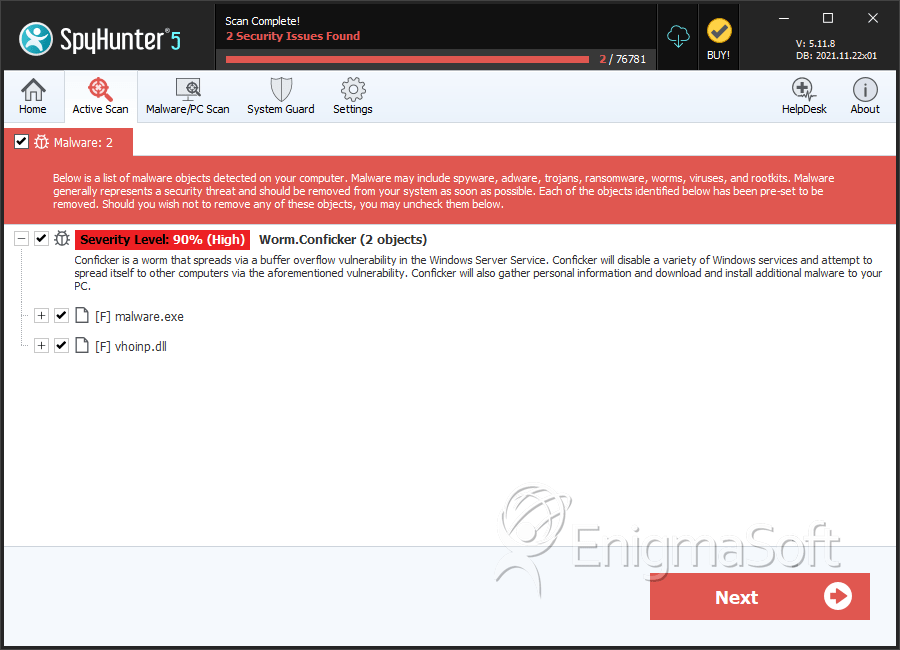
How to remove worm.conficker with the malwarebytes nebula console. While conficker is no longer the more. How to prevent getting conficker.
Disable the autoplay feature —which conficker uses to infect systems. Last october, microsoft released a patch designed to protect a computer running windows from the conficker worm. If you do not wish to download all windows updates but want.
Conficker set to strike: Although almost all of the advanced malware techniques used by conficker have seen past use or are well known to researchers, the virus's combined use of so many has made it unusually difficult to eradicate. Up to 24% cash back if you want to protect your computer from getting conficker then you need to do these simple steps.
How to remove conficker worm in 3 simple steps. If users cannot block these ports (and most probably admin will not be able to block 137. Use strong administrator passwords that are unique for all computers.
Pcworld mar 31, 2009 7:04 am pdt. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding. How do i remove conficker?
Cleaning steps (network) solution. Make sure your firewall is enabled when you are on untrusted networks. But industry action helped prevent the massive botnet the worm captured of millions of computers from fully being exploited.